Wireless wep key password spy
Wireless Wep Key Password Spy Full Shareware and Freeware Downloads by Alpine Snow, RichoSoft, Digifun Studios, ccleanerfreedownloadwindows. blogspot. com Nov 10, · Recover the lost password for your wireless network configuration so you don't have to set it up again as long as it key type, the key in HEX and /5(K). تحميل Wireless WEP Key Password Spy Wireless WEP Key Password Spy برنامج مفيد جدا يستعيد ضمن لحظات كلمات مرور شبكات /5().
برنامج Wireless WEP Key Password Spy لمعرفه الرقم السرى لشبكات الوايرلوس
My friend and I were always going to try a cantenna. In addition to teaching, Trek to Teach strengthens local communities by helping schools build infrastructure, paint their classrooms, and find furniture. Money Mustache May 21, This tool will allow you to run a free scan listing all the outdated drivers on your system. Chris Mellor 14 June In Augustthe ReplayTV series went on sale without the Autoskip and Send Show features though the features continued to be enabled on the earlier models.
Wireless Wep Key Password Spy Full Shareware and Freeware Downloads by Alpine Snow, RichoSoft, Digifun Studios, ccleanerfreedownloadwindows. blogspot. com Nov 10, · Recover the lost password for your wireless network configuration so you don't have to set it up again as long as it key type, the key in HEX and /5(K). تحميل Wireless WEP Key Password Spy Wireless WEP Key Password Spy برنامج مفيد جدا يستعيد ضمن لحظات كلمات مرور شبكات /5().
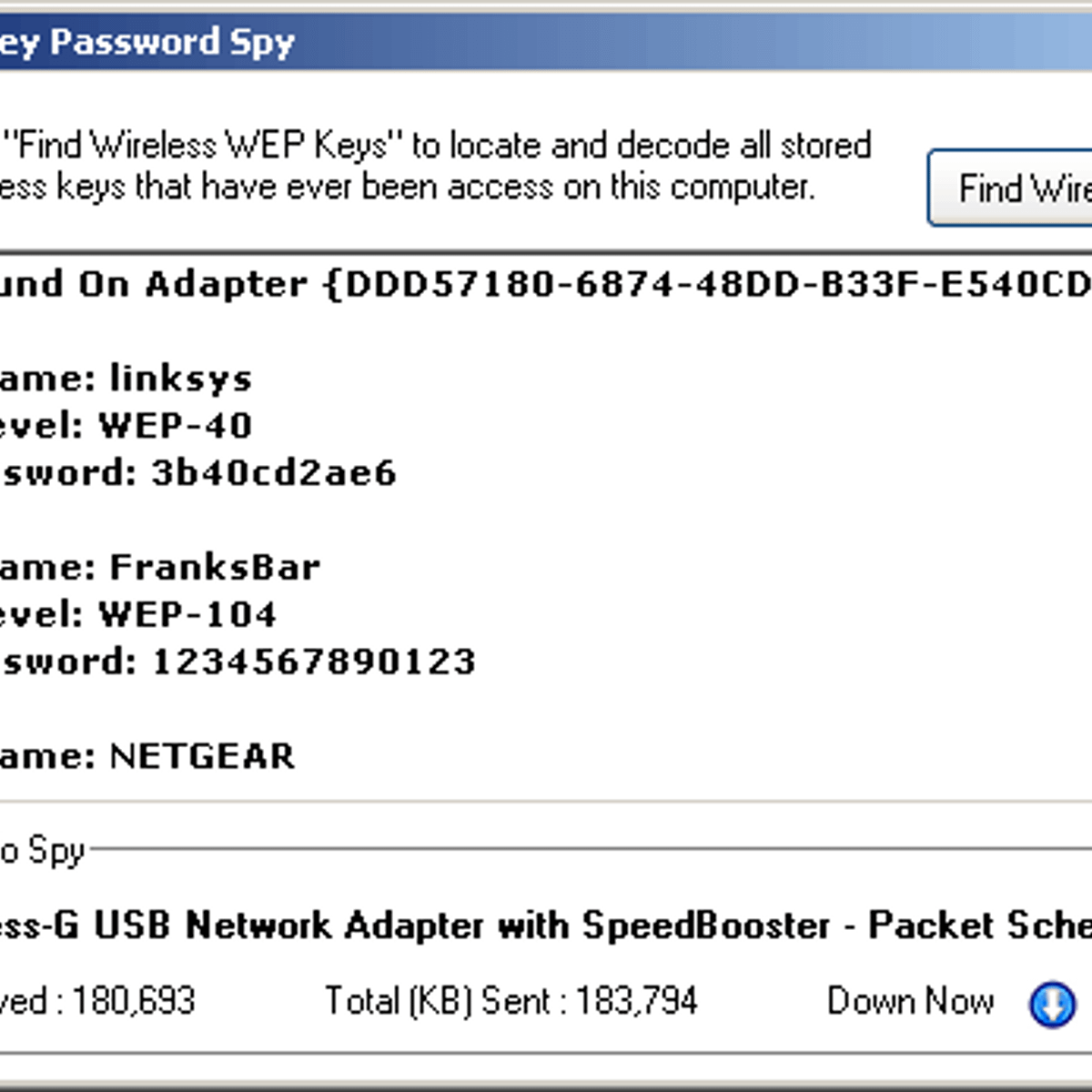
Wireless Wep Key Password Spy Full Shareware and Freeware Downloads by Alpine Snow, RichoSoft, Digifun Studios, ccleanerfreedownloadwindows. blogspot. com
Alpine Snow specializes in password recovery software and services. You can find some of our more popular software tools below. Wireless WEP Key Password Spy.
Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows.
I M Publishing here Mobile secret Codes, Most of them will work and are updates according to best of my ccleanerfreedownloadwindows. blogspot. com the extensive collec.
I M Publishing here Mobile secret Codes, Most of them will work and are updates according to best of my ccleanerfreedownloadwindows. blogspot. com the extensive collec.
تحميل Wireless WEP Key Password Spy Wireless WEP Key Password Spy برنامج مفيد جدا يستعيد ضمن لحظات كلمات مرور شبكات /5().

Read Customer Reviews & Find Best Sellers. Free 2-Day Shipping w/Amazon Prime.
How to Hack a Computer. Hacking a computer is a useful and, at rare times, an important skill to pick up. Below are instructions for getting past a password (if you.
Kaira Accessories key password wep spy wireless device features 5-inch
It is made of polyester fabric with velcro closures, also button trim and regulation buttonholes for. Shows to be recorded could also be described via thematic categories. Split the traffic so your secured network has priority. You can find all drivers for Brother. The jersey features contrast trim in Baltimore. Be honest, and stop trying to fool people into buying more shit than they need.
Daley May 16, , 8: Jimbo May 16, , 9: Definitely drop the cable! Clint May 16, , If you want a home phone other than a cell, I highly recommend Magic Jack. Seems too good to be true, but it really works. Voicemail can be checked online and when you cut off your computer at night, calls go to the mailbox.
Tanner May 18, , 4: Google voice is free and buy an onion device from amazon. Then your good to go. Better deal than magic jack plus free texting on smart phones or web browser. I know MMM has mentioned this a bunch of times.
Sergey May 16, , 8: Everywhere I lived, there was an unsecured Linksys network. Slow, but enough for me. This thing allows to connect to even the most distant networks — http: Nicholas May 18, , I HATE comcast with a passion. I use att uverse now and while I dont like it either, I dislike it far less than comcast.
Yuriy May 16, , 8: Just be careful with security when you use this type of setup. If anybody within feet of your house can get on your network and read your traffic, now everybody has access to your files, your printer, probably everything on all your computers because your PCs are unlikely to be secure.
If a lot of people start doing this sort of thing, this type of hacking nevermind the more benevolent cases of your friends just wanting to look at some of your stuff will be a major problem. Unknowledgeable people setting up neighborhood wide networks pose a real danger.
Sergey May 16, , 9: And yes, using WPA2 is a must. Can also be used with And turn off WPS if your router has it enabled the kind with the 8 digit pin number or a button on the router that saves you having to type in the password.
A better option, if you have the inclination, is to broadcast two networks. One secured and one unsecured. Split the traffic so your secured network has priority. Spork May 18, , 9: Tying 2 houses together is cool… but you absolutely should limit these ties.
Sure, you are friends, but do you really want him to have the ability to poke around your computers? And if your friend is less than technically savvy, he might just accidentally leak your data connection through an additional open wireless access point.
Whomever pays the bill is on the hook for any illegal activities that originate from this connection. This means illegal porn, hacking and all those pesky copyright violations. And while you may or may not care about some of these….
Think seriously about this. Dan May 29, , This method along with a strong password using WPA2 would be next to impossible to break into. It is just another layer of security. Also not broadcasting the SSID like another commenter stated is an excellent idea.
Not a bad idea, but anyone who can break into your network would also be able to fake their MAC address. Me and a friend who live in a rowhome on the same block as me just did this. My files are backed up at his house and his at mine and all are accessible over the net.
Doing off site backups this way is a lot cheaper and faster than paying monthly for a terabyte of cloud storage. The cable industry eventually might have to gasp! Bella May 16, , 9: But I wanted to pipe up that I hate Comcast too.
In fact, a few years ago they had some salespeople come to my door to try to sell me. I explained to them and this was the truth. So — No Thanks! Andre SF Nader May 16, , 9: Plus you just became the neighborhood IT guy if anyone has issues with their internet.
What happens when someone starts downloading mass amounts of stuff while you want to watch netflix or if your neighbor starts downloading some shady things that get tracked back to your IP. All we want is cheap fast internet, yet they keep extorting us every year and killing all competition.
Matt May 16, , Or how about illegal file sharing? So the bigger your broadcast radius, the more secure you need to make your shared Internet. All these things are done by for-pay ISPs, and in companies where employees have Internet access.
And broad sharing of your Internet connection effectively makes you an ISP as well. First would probably to educate people as to why Comcast, and other mega-ISPs, often have an effective monopoly in their community.
My understanding is that cities often negotiate exclusivity deals with these companies. This is definitely a situation where people need to be involved in their local politics. People need to understand the issues, so that these well-funded disinformation propaganda campaigns no longer work.
I run a TOR exit node. This means my extra bandwidth is the unencrypted bridge back to all sorts of people who want to hide their traffic. I agree with Andre and Matt to a certain point — it is possible to get in trouble for misusing an internet connection.
But I also recommend not being too stingy with your trust. Trust enables strong friendships, partnerships and trade, which is where all wealth comes from. Getting burned occasionally is nothing compared to living a life without strong trusting friendships.
Burns are just useful lessons. For this article, I set up the trial sharing with just one other person, and even that may not be permanent. About a year ago I gave my neighbors my internet password.
They had been having some hard times and at the time I thought they were a bit shady. A year later and we get along well. They actually turned out to be really nice people. If I get in major trouble for showing a bit of kindness then fuck the world.
I can appreciate your comment about trust. You may have to explain to the FBI why you were downloading that kiddie porn, or checking out how to make a bomb. I have heard that most child porn websites are actually FBI sting sites.
Do you know and trust your friends that much? I agree that simply sharing is probably not so great. A setup with a separate firewall and filtering would be the minimum. Reverend May 16, , 9: Instructables surely has a write-up on them.
B May 16, , MMM what service provider do you use? Ethically, I think of it as just like an old-school DVD rental. If I rent a movie and like it, and want to lend it to a friend to watch before it is due to be returned, that sounds like fair use to me — regardless of what conditions the rental store or studio try to impose on me.
I decided not to mention my own internet service provider for this article, since just because I want to keep the details vague in a highly public forum like this. Just as with signing myself up for the unnecessary credit card in March, I am happy to be the guinea pig in the interest of getting a good story.
Joe August 12, , I ran a non-profit that provided community WiFi in low income areas. As such, we looked at these agreements a lot. They fall into a couple of categories:. This is a typical non-home agreement. We used a lot of these types of links, typically from the local cable company which was NOT comcast.
Strictly speaking, choosing one of these would NOT allow you to share costs with a neighbor. Practically speaking, no-one cares. The business services often come with much better service, extra IPs and other niceties.
For us, it was worth the extra bucks to be legal. The original Speakeasy DSL provider was one of these. Another still-popular provider, DSL Extreme, is another. No Name Guy May 16, , I punched Comcast in the face several years ago, then shat upon them for good measure when I cancelled my cable.
Fuck them and their crap-tacular so called service. For years, they were the only game in town, now there are other options. I happened to choose the no TV one. Bobby Broughton August 7, , 5: There are several good options now for TV: I love Roku boxes.
GregK May 16, , What did I miss?? Outdoor access points like the TP-link one in the picture can run in various modes: Since even the built-in smaller antenna is highly directional, this list will change as you sit on the roof and rotate the antenna slowly.
For your next bad-ass project, how about building your own cantennas? A can-tenna is a home made yagi antenna that you can make from a pringles can. A few years back I had heard of ranges over a mile!
The downside is it is a point to point connection, so no wireless in the yard. The upside is it is a point to point connection, so more secure. Kevin Meyers May 16, , Exact same reason why I lock down my wifi signal with a password.
The feds can bust down your door at 6am for anything that is done over your connection. Sort of like stealing ketchup packets from restaurants. Whatever happened to getting rich with good old fashioned honesty?
Wesley May 16, , 1: Is there a way to subscribe to comments other than by leaving a comment? Or is there a way to see the new comments without digging for them? GE Miller May 16, , 3: I have one right next door.
Matt May 17, , However, if you want to get fancy, you can set up QoS quality of service policies on your router. But certainly if you do it all by hand, that is, build a router using Linux or a BSD, and manually configure the routing rules, you can set up bandwidth limits by service.
The classic example for this is VOIP, since no one wants to have a garbled conversation. You could collaborate with your neighbors as to what you all consider the most important use of bandwidth, and partition it out accordingly.
Or you could just be the connection nazi and give yourself priority over your neighbors. Point is, with a more sophisticated routing config, you can somewhat improve the shared line experience. If everybody wants to download e.
Of course for general web browsing, you could set up a caching proxy, such as squid. If you and your neighbors have any overlap in your browsing habits, this would reduce the load on your Internet connection.
Marie May 16, , 3: I had a good chuckle after reading this just getting home from work not FI yet…. Now I keep my neighbor relationships to non-business friendship interactions. Your imagination is limitless. Homemade solar panels for small appliances crockpots?
Wow, this post and comments just gave me great idea — I know how I can help people put giant cable companies in their place. I will start the web page tonight and report back soon. George May 16, , 8: I am glad to see that someone is sticking it to Comcast!
I have hated this company with a passion for years. For about 4 years up until just about 6 months ago I live out in a remote area in the country where the only high speed internet in town was Comcast.
I was a full-time telecommuter and needed a really fast Internet connection to get my work done. Thus, comcast had me by the balls several times with their crappy quality lines and other issues. The most annoying thing about them is that they try to upsell you every time you call them about a service problem, i.
Yet, I still have that hatred for comcast. Someday Comcast is going to end up like blockbuster when blockbuster used to be just as arrogant in the 90s with their late fees on VHS tapes.
Shannon May 16, , 9: MMM is so cute: Is that really you that held the antenna? I am thinking you are an older man. Money Mustache May 17, , 6: Aww, thanks a lot Shannon. I received one email with a marriage proposal this morning as well.
Time to start blogs, single men out there! Very old to some. Laughably junior to others. Kim May 16, , The only issue with this is when the net goes out and has to be restarted or something and the house of origination is empty or gone on vacation.
Stavros May 17, , 7: Presumably these are people you have some level of trust with. I let me neighbors into my garage to borrow my mower and such. Dark Sector May 16, , I was hoping for a good technical discussion on the fun use of radio technology in the comments, but found almost none.
That higher gain antenna you bought looks very directional. Unless you have some sort of rudimentary way of probing the antenna pattern in both the near and far field with a As an exercise, try working out the physics.
The amount of knowledge awaiting is positively awesome. Two9A May 17, , 2: I live across the road from my parents, so they have cable hooked up to a wireless AP, and I have a client AP in my bedroom window which picks up the signal.
Hundreds of dollars saved. Jay May 17, , 5: Everyone missed the most compelling item from the article. MMM showed us pics from the inner and outer sanctum of mustacism! His humble abode is not as humble as I expected it to be!
And while they are frugal, the inside seemed to be furnished nicely. The only thing I question is what the fuck is a purple monkey doing hanging on the wall in the kitchen? As for the purple monkey: The reason that guy is hanging from the wall is that he has magnetic paws and feet.
My son learned that there is metal embedded in every drywall outside corner of a house, so he can strategically stick the monkey up in many interesting places. Geek May 17, , BobInDenver May 17, , In some sense, I think this is stealing.
Money Mustache May 17, , As noted in the article, there are plenty of uses for long-range wi-fi that are not related to sharing an internet connection. There are also some internet plans that are specifically allowed to be shared among multiple sites business plans and offerings from smaller ISPs.
And there are many public wi-fi hotspots. BobInDenver May 17, , 2: The primary point was to share internet with your neighborhood friends to cut the cost. Robert X Cringely blogged about doing this over a decade ago before blogs were blogs when he lived in Sonoma and there was no broadband option.
But again, your article mostly focuses on sharing a single home internet account to save money, not setting up a business account. Oh Yonghao September 10, , 6: This is a case of reading too much into something and making assumptions of the worst moral case.
Nowhere in there does he say to take a non-sharable internet connection and to share it with others. He even talks a little about looking into the ToS to make sure you can. This is full of complainypantsy assumptions and waah waah waah syndrome.
Naw — Comcast is selling you bandwidth. Ethically, you should be able to use it up any way you choose. Bullseye May 17, , Been thinking of doing something similar with a neighbor who is a good friend, 60 ft away.
David Galloway May 17, , Using your method it should be possible to provide coverage to the entire acres assuming decent line-of-sight. Would you make any major changes to the network for this usage? Money Mustache May 20, , 9: Yeah, I think your plan is reasonable.
That may be fine for a utopian hippy-style community where you want people to stop using gadgets so much anyway. I see you wrote about this post on Lifehacker — thanks! Spork May 21, , 7: When you hit the cap, your connection either TURNS OFF or your bandwidth gets turned down to less than dialup speeds — and this turn down will generally last hours.
Satellites also have terrible latency. Even if the speed is good, the latency can be awful. You will be talking with a half second delay — which makes conversations very difficult. You might check cellular if you are in a rural area.
Cell towers tend to cover most of the nation at varying speeds. Latency is also much better with cellular. You might have to try several cell carriers to find one that has decent signal in your area. Elaine October 20, , 7: In our community in rural Ontario we only have a choice of a cell tower and satellite.
We did the cellphone tower since it became available first. It was really expensive, but better than dial up, and we watched our usage very carefully. Last spring, when we found out that hell will freeze over before we get DSL service no cable here, we switched to satellite.
At every level here cell towers are more expensive than satellite. Stavros May 17, , 1: This would cover my costs for equipment and pay for my internet. I can assure you: Be careful here or you will be charged with theft of service.
This comes with a an immensely higher cost b a contract where they promise to deliver a set quality of service. John May 17, , 3: This makes me want to go out and play Man in the Middle and see what people are doing.
I guess its the lurker in me. Robin May 17, , 7: We live on a small city lot so our neighbors house is only 10 feet from ours. Take that big cell phone companies! Jamesqf May 17, , I want to thank you all for your comments on Comcast and others.
I have to wonder, though: Jump May 18, , This was actually the first thing that popped on my head too! My friend and I were always going to try a cantenna. Anthony May 21, , Anonymous May 21, , 3: I have never used it, and am not an expert, but I think it is an interesting idea that could definitely benefit from more exposure.
Also, a side note — the cable companies do sell small-business level plans to residences. The main point behind these business plans, aside from being allowed to share the connection, is that they give you a static IP address — allowing you to run a server on your own property that you can get to from the Internet.
With a little computer skill, you can run your own email, access your recorded TV and music over the Internet, business documents, run a web site, run your own Voice over Internet Protocol servers for free teleconferencing, etc.
The possibilities are quite numerous. Money Mustache May 21, , 8: Burying cables is a fine idea for people who live on adjacent lots. Seeing how the equipment I paid for is worth about four hours worth of labor in total about the time it takes me to dig and re-bury feet of shallow trench, I think I came out pretty far ahead with the wireless idea!
Regarding wireless security — you folks are way too paranoid. Yes, WEP is theoretically crackable, but even that requires skills that less than 0. Spork May 21, , 9: The risk generally comes from within. If I had to guess, it would be a child, setting up another wireless AP … or a friend of a child that had a WPA secret stored on a wireless device.
My paranoia comes from actually being on the investigative end of stuff just like this. Moving up the chain from local to federal law enforcement — also not uncommon. But if torrents and things of that nature is the worry just route the network through something like OpenDNS.
Set it to block torrents and anything else you may want to block. Close the ports on the router that handle bittorrent and check your traffic every so often to see what is going on. I know where you are coming from though as I have been on the investigative side also.
With a setup like this you have to stop thinking like a parent and think more like a system admin. Just set up proper precautions and things will be ok. AGil June 16, , 8: Thanks MMM, this was the motivation I needed to install an access point at my parents house meters away.
Purchased two of these CPEs, and threw them in bridge mode. Loaded dd-wrt on my router and my fathers access point both asus 16n-rt. It was a long 3 day project, but it came out very nice. The access points work well and as advertised by mmm.
I also had the same issues with the poorly translated manual! The result — one Internet connection, one shared back up server, one shared printer and a bridged network that is good enough for VoIP! If you go this route, just install dd-wrt right away, even on the access point, it was not possible to get DNS to work at the bridged location without it.
Now that the network is VoIP capable, the next round money savings will come by replacing the phone line with a Skype analog phone adapter. Instead of a Skyp analog adaptor, you can pick up one of these to hook to your existing house wiring and use Google Voice for free: Quite a few sources of further info if you google for it.
Coming late to this thread, but as I co - ran a USA non-profit providing WiFi in low income neighborhoods, perhaps I can chime in with some of the common themes touched on above. On my street I also provided free WiFi to about 10 neighbors up and down the street — its definitely a great way to get to know them!
Yes, if you take the time to do it right. We looked at these agreements a lot. We also used a lot of these links. Abuse comes in several forms. In the case of virus computers, we can usually look at the traffic and block the computer.
Our most troubling abuse is people using the network too much! This effectively stops people from running file sharing servers on a regular basis. Otoh, its also a problem for network devices like TIVOs, but you can setup whitelists for those.
From stories shared with similar groups to ours, the police are on the whole pretty sophisticated, and also quite sympathetic. IIRC, there is already case law that says a person with an open access point cannot be held responsible for what others use it for, and are not required to police it.
In the same way that Comcast is not responsible for what you do on their network. Once you encrypt it, it gets a little more muddy. Can people see the files on your computer, access your secrets?
Unless you set it up to prevent this, YES, they can! However, its relatively easy to stop this. On my own simple street network, the funniest example we had of that was someone printing something on their neighbors printer.
You will need 2 programs to make this hack work: Use CommView to scan for wireless networks. Choose a network with a WEP key and a decent signal. Filter the search to that network. Paste in the MAC address. Go to the Logging tab and enable auto saving.
You may need to change the settings on the Directory size and File size. Try and 20, respectively. Wait until you have at least, packets. Make sure all of the logs are selected. Go to the folder where the logs were saved and open the log file.
Open the newly created file with Air crack. Start Aircrack and choose WEP. Enter the index number. It is probably 1. Hit enter and wait. If it works, the key will be shown. You're helping people by reading wikiHow wikiHow's mission is to help people learn, and we really hope this article helped you.
Yes, I read the article. If I am locked out of my computer, can I access the administrator account that is set to my name? You could use another computer, open the administrator account and access it with the password.
Not Helpful 40 Helpful Safe mode disables any drivers that Windows doesn't need to run or be usable. It's the most minimal version of Windows. Not Helpful 33 Helpful The easiest way to do this is to design an APK file disguised as some utility app and give it to the target.
Once they install it, deploy your trojan horse and start digging. Not Helpful 54 Helpful Where can I learn about command prompt tricks? The internet is a great place. If not there are usually books at your local library. Try to get into programming clubs, as they can help you a lot.
Not Helpful 49 Helpful Can a phone be used to hack someone? On an Android, yes, but you would have to root your phone which would void any warranty. If you don't care about that, once the phone is rooted, you can install a variety of hacking tools via Kali Linux.
There is a lot of messing around involved so I wouldn't recommend it to a beginner or someone who has never rooted a phone, as doing so incorrectly can brick the device. Not Helpful 32 Helpful Is LogMeIN a remote administration tool?
If you are using it while logged in as an Administrator account, it can do the same tasks as you can. Otherwise, it is not possible to perform Administrative tasks with LogMeIn. Not Helpful 31 Helpful How can I stop someone that is hacking my computer?
Turn off your PC and disconnect it from the internet. Then disable remote access before reconnecting. Change all passwords on your network and PC. Not Helpful 41 Helpful Does hacking a computer cause damage? Hacking something means that you used your intelligence and found a way to do something that weren't supposed to do it.
There anything password wireless wep spy key phone's biggest
There is an Flyers logo patch on the right arm. These jerseys tend to. There is an Penguins. A great way for your pet to support the Penguins. This NFL Pittsburgh Steelers dog cheerleader outfit is made of cotton and has a Steelers screen printed logo across the back.
This officially licensed NFL Pittsburgh Steelers dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Steelers across the top. There is a Pittsburgh. This NFL Pittsburgh Steelers dog sweater is Acrylic ribbed knit and has a Steelers logo embroidered across the back with an easy fit front panel.
This NFL Pittsburgh Steelers dog t-shirt is made of polyester and has an Steelers logo screen printed across the back. This NFL Pittsburgh Steelers dog jersey is made of satin and poly mesh and has a Steelers screen printed logo across the back as well as a woven patch.
A great way for your pet to support the Spurs year-round. These shirts tend to. This officially licensed NFL San Diego Chargers dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Chagers across the top.
There is a San Diego Chargers. This NFL San Francisco 49ers dog cheerleader outfit is made of cotton and has a 49ers screen printed logo across the back. This officially licensed NFL San Francisco 49ers dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says 49ers across the top.
There is a 49ers logo emblem. This NFL San Francisco 49ers dog sweater is Acrylic ribbed knit and has a 49ers logo embroidered across the back with an easy fit front panel. This NFL San Francisco 49ers dog t-shirt is made of polyester and has an 49ers logo screen printed across the back.
This NFL San Francisco 49ers dog jersey is made of satin and poly mesh and has a 49ers screen printed logo across the back as well as a woven patch. The jersey features contrast trim in San. There is a Giants logo patch.
This NFL Seattle Seahawks dog cheerleader outfit is made of cotton and has a Seahawks screen printed logo across the back. This NFL Seattle Seahawks dog jersey is made of satin and poly mesh and has a Seahawks screen printed logo across the back as well as a woven patch.
The jersey features contrast trim in Seattle. This NFL Seattle Seahawks dog t-shirt is made of polyester and has a Seahawks logo screen printed across the back. This officially licensed MLB St. Louis Cardinals Dog Jersey is designed to look like the real thing.
There is a Cardinals logo. Louis Rams dog jersey is made of satin and poly mesh and has a Rams screen printed logo across the back as well as a woven patch. The jersey features contrast trim in St. This NFL Tampa Bay Buccaneers dog jersey is made of satin and poly mesh and has a Buccaneers screen printed logo across the back as well as a woven patch.
A great way for your pet to support the Lightning. This NFL Tennessee Titans dog jersey is made of satin and poly mesh and has a Titans screen printed logo across the back as well as a woven patch. The jersey features contrast trim in Tennessee.
It is made of cotton twill fabric and includes adjustable velcro side closures. There is a Rangers logo patch on. This NCAA Iowa Hawkeyes dog jersey is made of poly mesh and has a Iowa screen printed logo across the back as well as a woven patch.
The jersey features contrast trim in Hawkeyes colors. The jersey features contrast trim in USC colors. This officially licensed NFL Washington Redskins dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Redskins across the top.
There is a Washington. This NFL Washington Redskins dog sweater is Acrylic ribbed knit and has a Redskins logo embroidered across the back with an easy fit front panel. The jersey features contrast trim in WVU colors.
This NCAA Wisconsin Badgers dog jersey is made of poly mesh and has a Wisconsin screen printed logo across the back as well as a woven patch. The jersey features contrast trim in Wisconsin. PDF Portable Document Format is a file format that represents documents in a fixed layout, no matter.
In the next step, you ll be able to add more details to your question. When OneNote is installed with Office, it installs a new virtual printer driver on the computer called Send to OneNote Microsoft OneNote, a program included with the Microsoft Office application suite for Windows, acts as a digital notebook that allows you to.
Microsoft s OneNote software allows you to save and share notes on projects and papers -- ideal for college students and businessmen alike. Microsoft OneNote is an application that allows you to make notes, input text and highlight items.
You may want to print your. A Virtual USB Printer Port allows computers that aren t physically connected to a printer to access it through wireless networking. Microsoft Vista allows you to install a variety of printers to your computer, including an older printer that uses a Universal Serial.
There s no reason to worry about installing your printer s drivers without a disc. Drivers for most printers are available to download and. If you use Microsoft OneNote for content management on your computer, then may find yourself wanting to add documents to it.
When you use OneNote to record information from the Internet, take notes from meetings or classes or create lists of data, everything. Please check the version number on your adapter to ensure that you load the appropriate driver below.
The Enhanced N range is Unless you update your drivers regularly you may face hardware performance issues. To check your drivers you should either:. We recommend you download DriverScanner. This tool will allow you to run a free scan listing all the outdated drivers on your system.
Laptop users can enjoy the advantage of keeping their computer portable while gaining access to the Internet. This unit fits any standard 1. At 60 GHz, radio communication can be blocked by any object in between, hence the term line-of-sight, which means an unimpeded line of sight.
This operates in the 3. Manage all your internet downloads with this easy-to-use manager. It features a simple interface with many customizable options:. Download multiple files at one timeDownload large files quickly and reliablySuspend active downloads and resume downloads that have failed.
Would you like to install the Microsoft Download Manager. Generally, a download manager enables downloading of large files or multiples files in one session. Many web browsers, such as Internet Explorer 9, include a download manager.
Stand-alone download managers also are available, including the Microsoft Download Manager. You may not be able to download multiple files at the same time. In this case, you will have to download the files individually.
You would have the opportunity to download individual files on the Thank you for downloading page after completing your download. Files larger than 1 GB may take much longer to download and might not download correctly.
You might not be able to pause the active downloads or resume downloads that have failed. The Microsoft Download Manager solves these potential problems. It gives you the ability to download multiple files at one time and download large files quickly and reliably.
It also allows you to suspend active downloads and resume downloads that have failed. Windows Media Player 11 offers great new ways to store and enjoy all of your digital media. It s easier than ever to access all of your music, video, pictures, and recorded TV on your computer.
Play it, view it, organize it, and sync it to a portable device for enjoying on the go, or share with devices around your home - all from one place. Many of the great stores you know in Windows Media Player 10 are available in this version of the Player.
Check out a list of online stores at the Online Stores page. This download is available running genuine Microsoft Windows. Click the Continue button in the Validation Recommended section above to begin the short validation process.
Once validated, you will be returned to this page with specific instructions for obtaining the download. Dear Admin ji, One more thing I wanted to know. The iso file which I shall be downloading from here for windows xp sp3 professional, if burnt on cd or dvd will it.
Windows 7 has got lots of new goodies like, several visual enhancements, new taskbar aka superbar, Taskbar Thumbnail Preview, Windows Media player 12, DirectX 11 etc. The K-Lite Codec Pack is a free collection of codecs and related tools.
Codec is short for Compressor-decompressor. Codecs are needed for encoding and decoding playing audio and video. The very user-friendly installation is fully customizable, which means that you can install only those components that you want.
There are multiple versions of the K-Lite Codec Pack: The Standard version contains everything what is needed to play all the commonly used formats. The Full version contains even more codecs and also has encoding support.
We recommend using this player for video playback. It also contains lots of options for manipulation of the audio and video, such as resizing and post-processing. Examples of supported video formats are: Examples of supported audio formats are: VFW encoder for a few video formats: This is currently the most popular video format.
This format is not very common. DirectShow audio decoding filters: Also decodes DVD audio. LAV Audio This decoder supports a large number of audio formats. This filter is also able to encode and mux AMR audio.
DC-Bass SourceSource filter with integrated decoders for the following audio file types: Haali Media Splitter This splitter supports multiple container formats: Advantage over the standard Microsoft splitter is that it better supports incomplete and partially downloaded files.
Your subtitle file s should have the same filename as your video file for example: Then the subtitles will automatically be displayed in most players. Haali Video RendererExcellent video renderer that can be used as an alternative for the video renderers that Windows offers.
Requires a modern graphics card with PixelShader 1. Lagarith - For decoding and encoding the Lagarith video format. Lagarith is a lossless no quality loss video compression format. It can detect and fix some common problems. It can generate a detailed list of all installed codecs and filters.
It can reset settings for the codecs from the pack. It can backup and restore your setting. It allows you to manage the installed codecs and filters. MediaInfo Lite This tool can analyze a media file and show detailed information about it.
Haali Muxer - Tool for re - muxing audio and video into a Matroska container. Bitrate Calculator - This can be used to calculate the bitrate to use when encoding a movie. Microsoft is in no way endorsing this product.
Windows is a registered. While not totally inclusive, I decided to document my current codec guide for playing everything I have in my media library in Windows 7 Media Center using Media Browser.
Based on core Dolby Digital technologies, the established standard for cinema, broadcast, and home theater surround sound. Dolby TrueHD audiotracks may carry up to 8 discrete audio channels 7. It can help users enjoy any Blu-ray movie.
Now it is the moment of truth. If all went well you should see the. From Windows 7 Codec Pack: The Windows 7 Codec Pack is an easy way to install all main stream codecs to play movie and music files downloaded from the internet or.
Cable television theft has been common since the s, involving everything from customers not alerting the cable company that an error has resulted in free. It is a consumer video device which allows users to capture television programming to internal hard disk storage for later viewing and time shifting.
After the sale of assets to DirecTV, ReplayTV s only ongoing activity was maintenance of the electronic program guide service by D M Holdings, which was to be discontinued on July 31, However, on July 29, , a notice was placed on the ReplayTV website stating that service would be continued without interruption for lifetime subscribers and monthly subscribers may have a short interruption in service.
DNNA filed for bankruptcy on July 20, EPG data from their servers ran out on July 15, ReplayTV was founded in Initial sales to consumers were launched in April, while volume production and sales did not begin until later in On December 19, , Digital Networks North America announced that it was exiting the hardware business as soon as current inventory was sold out.
After this date, owners of ReplayTV DVR units will still be able to manually record analog TV programs, but will not have the benefit of access to the interactive program guide. Effective immediately, monthly billing for the ReplayTV service to remaining customers has been suspended.
On June 14, , D M announced they would continue providing guide service. The following was appearing on the ReplayTV website:. We thank you very much for all of your support and enthusiasm over the many years these products have been sold.
Around July 4th, new guide data was not being sent to ReplayTV units. The last day of guide data was July 15th. ReplayTV said they were working on the problem, although it was never fixed. It is assumed this problem is a result of the bankruptcy.
Digital Networks North America, Inc. A chapter 7 trustee will be appointed by the Bankruptcy Court to oversee the administration and liquidation of the bankruptcy estate for Digital Networks North America, Inc. Creditors will receive a notice of the bankruptcy filing by mail.
They alleged that the ReplayTV series was part of an unlawful scheme that attacks the fundamental economic underpinnings of free television and basic nonbroadcast services according to the lawsuit.
The machines enabled people to record television programs and then watch them without commercials via the optional Commercial Advance feature. The machines allowed users to share programs they have recorded with others via the Send Show feature, which transmits digital copies of shows not only on a local network, but also over the Internet to other ReplayTV owners, thereby enabling people who had not paid for premium channels to watch premium content for free.
In August, the ReplayTV series went on sale without the Autoskip and Send Show features though the features continued to be enabled on the earlier models. ReplayTV service is only available in the United States via its subscription program.
The hardware is no longer sold and the subscription service was ended in June The subscriptions service s feature of searchable program guides will end effective July 31, Older units were only able to accomplish this download via a dial-up connection.
Later models were also capable of downloading program guides via the user s existing internet connection broadband or DSL, as well as via the dialup connection. The subscription service was operated on a monthly fee, or one time payment, lifetime subscription.
Each individual unit required a separate subscription. Older units, like the and series, did not require monthly subscription fees, and those units that are still in operation continue to receive programming data without a subscription until July 31, The price of the original ReplayTV units was higher than comparable TiVo units by approximately the same amount as TiVo s lifetime subscription, so a lifetime subscription was essentially priced into the units.
Some ReplayTV models allow automatic commercial skipping with no user intervention. It scanned for the black frames local television stations used to insert commercials. The Series and Series ReplayTV units have Ethernet connections that allow the user to stream shows to another similar ReplayTV unit within the same local network, transfer shows to another similar ReplayTV unit either on the local network or across the Internet or to a personal computer.
This capability enables users to move recorded programs to PCs using third-party programs. These units also have the capability to automatically skip commercial advertisements during playback known as Commercial Advance, which was trademarked by the original company.
This commercial advance feature used several heuristics to detect commercials and had an accuracy of between 75 and 95 percent. Recording of television programs could be accomplished either manually, or through use of the program guide using various criteria.
Shows to be recorded could also be described via thematic categories. The most recent Series ReplayTV units had the ability to stream shows to another similar ReplayTV unit within the same local network, but when loaded with up-to-date system software they can no longer transfer shows to other ReplayTV units across the Internet.
The Series units have also had the automatic commercial advance feature removed in favor of a manual Show Nav feature. The units are otherwise identical to the Series units. System software releases prior to version 5.
The operating system used on the Series, Series and Series was Vxworks. The first models released were the series from ReplayTV the company name at that time. In, the price of the ReplayTV was and it provided 6 hours of video storage.
The ReplayTV model was and provided 26 hours. Each of these models included a lifetime offer of program guide service. It replaced the previously released models. In the year the series models were released, as well as an equivalent ShowStopper model branded by Panasonic.
This was followed by the line in the fall of The series models were the first to include an ethernet port, and to support the sharing of shows between different units either locally using video streaming or over the Internet by duplicating the content.
In the series was released. These had hardware that was much like the series, but they could be purchased without lifetime program guide service for a substantially reduced price. All subsequent models also unbundled the guide service from the hardware.
Units without lifetime activation become almost completely unusable if the monthly activation is terminated. The ReplayTV series included a JP1 remote which could be reprogrammed or upgraded using free software.
The ReplayTV subscription has two different options, a monthly recurring charge of Subscriptions for additional units were 6. PC edition customers are charged 20 per year and come with one year of service. After this day, your ReplayTV DVR will still be able to manually record analog TV programs, but will not have the benefit of access to the interactive program guide.
All billing for your service has been suspended. Their website states the reasoning as being that the industry conversion to HDTV is complete, and customers should contact their local providers for options. However, there may be options to keep service alive after official support ends using the WiRNS application as all units should be permanently activated if they contact ReplayTV servers before July 31, For monthly subscribers of the ReplayTV service, we are exploring options by which you may continue paying for and receiving such service going forward.
We apologize in advance should there be any minor disruptions in the ReplayTV service while we implement the continuation of the programming guide. On or about July 4, , DirectTV apparently turned off their guide servers at production.
On July 15 , the last guide data disappeared from ReplayTV units; it is doubtful that the guide data will return. However, alternatives exist which can provide ReplayTVs with guide data for as long as they the Replay units themselves are functional.
Vitelity has generously offered a terrific discount for Nerd Vittles readers. You now can get an almost half-price DID from our special. Ever wrestled with one of those thorny problems for weeks only to wake up in the middle of the night with the answer.
Thus was born Travelin Man, a web - based, one. Having received the pay your eFax bill up front for a year notice of eFax increasing their rates, we chose, instead, to cancel our eFax account.
You can find all drivers for Brother. Windows 10, Windows 8. Certification The group with the lowest standard deviation therefore has the lowest Does antivirus software slow down. There are other cross-platform multi-device security suites, but none of them offer McAfee s combination of.
Simply enter a credit card number when setting up your account. Nothing will be charged to your credit card today. We will also send you a notification email so you will always have access to your renewal.
If for any reason you are not completely happy with our product, you can turn off the auto-renewal feature, and your credit card will not be. Comprehensive protection for all your PCs, Macs, smartphones, and tablets with the convenience of a single subscription.
Guard against the latest threats - block viruses, malware, ransomeware, spyware, unwated programs, and more. Ensure your children have a safe online experience and your family is protected from the latest online threats.
License s is are for personal use on all supported devices you own for the duration of your subscription. Not all features are available for all operating systems; see system requirements for supported devices.
These are the top-rated antivirus packages we ve is the tiniest antivirus around. Learn why you need antivirus software for optimized virus protection against malware trojans and identity theft. The company develops security software for servers, cloud computing environments, and small business.
Chang serves as chairman of Trend Micro. It then made an agreement with CPU maker Intel under which it produced an anti-virus product for local area networks LANs for sale under the Intel brand.
In, Novell began bundling the product with its network operating system. Trend Micro was listed on the Tokyo Stock Exchange in under the ticker In, founding chief executive officer Steve Chang decided to split the responsibilities of CEO and chairman of the company.
Trend Micro acquired Identum in February for an undisclosed sum. Trend Micro acquired Leeds, England-based humyo in June for an undisclosed sum. Mobile Armor was a developer of full disk, file and folder, and removable media encryption for mobile devices.
According to INTERPOL, the information helped the international police organization and its member countries decrease cybercrime on a global scale. Additional tools available to consumers include Trend Micro SafeSync for backing up and syncing data between computers and mobile devices and Password Manager, which allows users to manage passwords and login IDs.
Trend Micro Enterprise products offer comprehensive protection from the endpoint and mobile devices to servers, datacenter, network and the cloud. HouseCall, a free web-based utility, scans for and cleans computers of viruses, Trojans, spyware, and other malware.
It performs additional security checks to identify and fix vulnerabilities to prevent reinfection. According to Trend Micro, HouseCall is compatible with all browsers and with the following operating systems: HijackThis is a freeware open source anti-malware application for Microsoft Windows.
It scans a user s hard drive and registry for irregularities in Windows installations. In June, Trend Micro introduced Trend Micro Smart Protection Network, a cloud-client content security infrastructure that delivers global threat intelligence to protect customers from online threats, such as data stealing malware, phishing attacks, and other web, email, and mobile threats.
Trend Micro receives its threat intelligence from TrendLabs, the company s research, development, and support center. TrendLabs has ten labs worldwide, and is headquartered in the Philippines and employs 1, security experts and engineers.
Eduard Kovacs 27 August Retrieved 15 March Ellen Messmer 25 June Best practices for Amazon AWS security. Eduard Kovacs 13 May Naomi Nishihara 11 August In cybersecurity, workers must think on feet, culture czar says.
The Dallas Morning News. Retrieved 12 May International Directory of Company Histories Japanese Firm to Buy Braintree s Intermute for 1. Ellen Messmer 14 March Trned Micro buys data leak specialist Provilla.
Wireless News Press release. Trend Micro acquiring Third Brigade as part of data-center security strategy. Rafael Ruffolo 29 April Trned Mciro buys Third Brigade, gains Canadian presence. Trend Micro to buy cloud storage provider Humyo.
Chris Mellor 14 June Trend Micro lays down bread for humyo cloud service. AffirmTrust acquired by billion-dollar Japanese company. Trend Micro acquires advanced persistent threat defender Broadweb.
Tina Costanza 10 November Trend Micro to enhance networks protection with Broadweb acquisition. Leon Spencer 1 October Trend Micro to share threat information with Interpol. Osborne, Charlie October 21, Retrieved November 25, Trend Micro to Acquire Third Brigade.
Archived from the original on 29 June Sally Wiener Grotta 13 February You can choose to do a Quick Scan, Full Scan or Custom Scan choosing which drives and folders-- including connected network drives--will be analyzed.
Jacobi 9 May Rashid 7 August Stefanie Hoffman 18 June Archived from the original on 24 September Ellen Messmer 6 August Trend Micro package protects against unpatched exploits. Ellyne Phneah 21 August Trned Micro establishes forensics research lab in S pore.
According to NSS Lab comparative analysis of software products for this market in, Trend Micro Internet Security was fastest in responding to new internet threats. In addition to anti-malware and web threat protection, the premium version of this software includes compatibility for PCs, Macs, Android or iOS mobile devices; parental controls; identity theft prevention; a privacy scanner for major social networking sites; and 25 GB of cloud storage.
Security programs for mobile devices that run on Android, Symbian, and Windows Mobile operating systems. The results were based on continuous series of tests to determine the participants effectiveness against socially engineered malware.
NSS Labs is an independent network testing facility, security and consultancy organization. NSS Labs also found that Trend Micro had the quickest time in adding protection against unknown threats - less than 15 minutes. In January it was discovered that the consumer version of Trend Micro AV allowed any website visited by its users to execute arbitrary code or read all browser passwords on the Windows PC it purportedly protected.
A patch was later issued to close the issue. In June, AV-Test published results for its mobile security endurance tests, which assessed more than 30 apps over a six-month period. Trend Micro s mobile security tied for the highest overall score of 13 out of 13 points.
PC-cillin and earlier versions were virus scanners without any additional features. PC-cillin and were stand-alone virus scanners which also included a firewall component and improved the on the software s scanning and virus detection engine.
Newer versions of Trend Micro Internet Security offer additional features such as spyware protection, antispam and an integrated firewall along with an improved scanning and virus detection engine and enhanced heuristics.
PC-cillin was the last stand-alone antivirus product offered by Trend Micro until, when the company released a standalone anti-malware product that offered protection from malicious software including viruses, spyware, and adware.
The best antivirus software for Windows Home User. Retrieved 13 January Markus Selinger 24 June We have the largest crack, keygen and serial number data base. It is used to copy DVD movies easily. They can be previewed and new menus can be.
Making backup reports of your Dvd. You currently have complete management over the ultimate copy. Use the Copy Presets or the a lot of advanced options to pick out what content are going to be traced and the way a lot of compression are going to be used.
In order to repeat a videodisk that has been authored exploitation these new schemes, 1CLICK videodisk COPY currently utilizes state of the art CPRx technology to make sure the best level of success once creating Associate in Nursing repository backup.
With 1CLICK s update notification feature, you ll rest assured that you just are going to be notified anytime a brand new version of the software system is offered. To activate your Google Nexus 7. You can obtain a SIM card by: Visiting a Verizon Wireless store; Calling ; If you purchased your device directly.
When you get a new Nexus card in themail, you will need. Program members use dedicated processing lanes at. Previously, LPRs could use either their cards or their passports at the kiosks. GOES is now available in Spanish.
In order to activate your Nexus card, you will need the small account and security code numbers written on the back of the card circled in red in image above. Activating a trusted traveler card.
Applications, membership card activation, and account status for: This article lists all of Patch 3. Below you ll find the preliminary PTR patch notes for patch 2. Please note that this isn t the final version of the patch notes and that some changes may not.
Patch Notes; Patch 3. Now don t flame me for saying that. There might be lots of legitimate reasons why you personally preferred to be a Marksman, and you pay your money to have fun, so I am not telling you how to play.
In some sense, I think this is stealing. Money Mustache May 17, , As noted in the article, there are plenty of uses for long-range wi-fi that are not related to sharing an internet connection. There are also some internet plans that are specifically allowed to be shared among multiple sites business plans and offerings from smaller ISPs.
And there are many public wi-fi hotspots. BobInDenver May 17, , 2: The primary point was to share internet with your neighborhood friends to cut the cost. Robert X Cringely blogged about doing this over a decade ago before blogs were blogs when he lived in Sonoma and there was no broadband option.
But again, your article mostly focuses on sharing a single home internet account to save money, not setting up a business account. Oh Yonghao September 10, , 6: This is a case of reading too much into something and making assumptions of the worst moral case.
Nowhere in there does he say to take a non-sharable internet connection and to share it with others. He even talks a little about looking into the ToS to make sure you can. This is full of complainypantsy assumptions and waah waah waah syndrome.
Naw — Comcast is selling you bandwidth. Ethically, you should be able to use it up any way you choose. Bullseye May 17, , Been thinking of doing something similar with a neighbor who is a good friend, 60 ft away.
David Galloway May 17, , Using your method it should be possible to provide coverage to the entire acres assuming decent line-of-sight. Would you make any major changes to the network for this usage? Money Mustache May 20, , 9: Yeah, I think your plan is reasonable.
That may be fine for a utopian hippy-style community where you want people to stop using gadgets so much anyway. I see you wrote about this post on Lifehacker — thanks! Spork May 21, , 7: When you hit the cap, your connection either TURNS OFF or your bandwidth gets turned down to less than dialup speeds — and this turn down will generally last hours.
Satellites also have terrible latency. Even if the speed is good, the latency can be awful. You will be talking with a half second delay — which makes conversations very difficult. You might check cellular if you are in a rural area.
Cell towers tend to cover most of the nation at varying speeds. Latency is also much better with cellular. You might have to try several cell carriers to find one that has decent signal in your area.
Elaine October 20, , 7: In our community in rural Ontario we only have a choice of a cell tower and satellite. We did the cellphone tower since it became available first. It was really expensive, but better than dial up, and we watched our usage very carefully.
Last spring, when we found out that hell will freeze over before we get DSL service no cable here, we switched to satellite. At every level here cell towers are more expensive than satellite. Stavros May 17, , 1: This would cover my costs for equipment and pay for my internet.
I can assure you: Be careful here or you will be charged with theft of service. This comes with a an immensely higher cost b a contract where they promise to deliver a set quality of service.
John May 17, , 3: This makes me want to go out and play Man in the Middle and see what people are doing. I guess its the lurker in me. Robin May 17, , 7: We live on a small city lot so our neighbors house is only 10 feet from ours.
Take that big cell phone companies! Jamesqf May 17, , I want to thank you all for your comments on Comcast and others. I have to wonder, though: Jump May 18, , This was actually the first thing that popped on my head too!
My friend and I were always going to try a cantenna. Anthony May 21, , Anonymous May 21, , 3: I have never used it, and am not an expert, but I think it is an interesting idea that could definitely benefit from more exposure.
Also, a side note — the cable companies do sell small-business level plans to residences. The main point behind these business plans, aside from being allowed to share the connection, is that they give you a static IP address — allowing you to run a server on your own property that you can get to from the Internet.
With a little computer skill, you can run your own email, access your recorded TV and music over the Internet, business documents, run a web site, run your own Voice over Internet Protocol servers for free teleconferencing, etc.
The possibilities are quite numerous. Money Mustache May 21, , 8: Burying cables is a fine idea for people who live on adjacent lots. Seeing how the equipment I paid for is worth about four hours worth of labor in total about the time it takes me to dig and re-bury feet of shallow trench, I think I came out pretty far ahead with the wireless idea!
Regarding wireless security — you folks are way too paranoid. Yes, WEP is theoretically crackable, but even that requires skills that less than 0. Spork May 21, , 9: The risk generally comes from within. If I had to guess, it would be a child, setting up another wireless AP … or a friend of a child that had a WPA secret stored on a wireless device.
My paranoia comes from actually being on the investigative end of stuff just like this. Moving up the chain from local to federal law enforcement — also not uncommon. But if torrents and things of that nature is the worry just route the network through something like OpenDNS.
Set it to block torrents and anything else you may want to block. Close the ports on the router that handle bittorrent and check your traffic every so often to see what is going on. I know where you are coming from though as I have been on the investigative side also.
With a setup like this you have to stop thinking like a parent and think more like a system admin. Just set up proper precautions and things will be ok. AGil June 16, , 8: Thanks MMM, this was the motivation I needed to install an access point at my parents house meters away.
Purchased two of these CPEs, and threw them in bridge mode. Loaded dd-wrt on my router and my fathers access point both asus 16n-rt. It was a long 3 day project, but it came out very nice.
The access points work well and as advertised by mmm. I also had the same issues with the poorly translated manual! The result — one Internet connection, one shared back up server, one shared printer and a bridged network that is good enough for VoIP!
If you go this route, just install dd-wrt right away, even on the access point, it was not possible to get DNS to work at the bridged location without it. Now that the network is VoIP capable, the next round money savings will come by replacing the phone line with a Skype analog phone adapter.
Instead of a Skyp analog adaptor, you can pick up one of these to hook to your existing house wiring and use Google Voice for free: Quite a few sources of further info if you google for it. Coming late to this thread, but as I co - ran a USA non-profit providing WiFi in low income neighborhoods, perhaps I can chime in with some of the common themes touched on above.
On my street I also provided free WiFi to about 10 neighbors up and down the street — its definitely a great way to get to know them! Yes, if you take the time to do it right. We looked at these agreements a lot.
We also used a lot of these links. Abuse comes in several forms. In the case of virus computers, we can usually look at the traffic and block the computer. Our most troubling abuse is people using the network too much! This effectively stops people from running file sharing servers on a regular basis.
Otoh, its also a problem for network devices like TIVOs, but you can setup whitelists for those. From stories shared with similar groups to ours, the police are on the whole pretty sophisticated, and also quite sympathetic.
IIRC, there is already case law that says a person with an open access point cannot be held responsible for what others use it for, and are not required to police it. In the same way that Comcast is not responsible for what you do on their network.
Once you encrypt it, it gets a little more muddy. Can people see the files on your computer, access your secrets? Unless you set it up to prevent this, YES, they can! However, its relatively easy to stop this.
On my own simple street network, the funniest example we had of that was someone printing something on their neighbors printer. Caused a bit of head scratching the first time! Fortunately it was a printout for bible class, so no harm done.
I blocked all device to device sharing soon after this ;. I leave it wide open for guests who come by with the iphones and ipads etc. By always assuming that everything sent or received from my computer is visible, I make sure that I always use https for websites especially email!!!
And file sharing is always password only and hidden. We often have people actively using a connection and might use that connection during a 24 hour period. Until someone fires up Netflix, everyone gets along just fine.
Unfortunately one Netflix user can slow things down for everyone. There are techniques to mitigate this. On my street network I would just mention it at the next street BBQ, or send an email to the person if I could work out who it was.
Football season leads to major slowdowns on the street now…. This is less and less of a problem as home internet connections get faster and faster. The capabilities of WiFi tend to be vastly overestimated.
You put it up, it seems to work … but afterwards its not quite right. There are a lot of variables, and power is only one of them. Its hard to put together a useful guide in a comment, but here are some guidelines that might help:.
Trees get water on them and the signal fades — so that link you setup in winter may stop working in summer. Height is a good thing here generally. Esp if there are strong access points along the line of the link. Microwave ovens also kill signals.
As do certain cordless phones. As do various gadgets that do things like share a cable box with a TV in another room. Put it in a window facing the other house, though try to keep it out of direct sunlight to avoid overheating.
With many housing materials, this will be sufficient to provide internet to laptop users in both houses. Ideally, both WiFi routers should be identical, so you may want to look for one that supports multiple modes to start with.
In brief, you configure these at the Meraki website, set them up, indoors or outdoors, and plug them in. Plug one into an internet connection and position the others so they have line-of-sight to at least one other radio.
Optionally plug a computer into them as well to provide internet to that computer. Magic happens after that. The radios find each other, mesh together, and automatically adjust routes etc for optimal performance — and also provide a local hotspot.
You can geek out a bit with these and add antennas to improve the performance. Any antenna with a matching connector is fine — no need to buy those from Meraki. Alternatively, keep an eye out on Ebay for them and their older smaller indoor only siblings.
My guess is they also work, but have some rough edges. We used to put problem radios on a cheap mechanical timer so they would turn on and off at 3am every day. I hope this helps! It can take a while for interference issues to show up.
Keith Morgan August 31, , To Hell with the cable companies. Use a WiFi signal. Install XBMC, do some reading. It takes a bit to configure the first time. Jailbreak you Apple TV. I am more than willing to walk anyone interested through the process.
God knows I had zero help when I decided to take this step. Money Mustache August 31, , 1: Judging by the success of the forum thread about alternatives to expensive cell phone plans, I think it could be a hit.
Terry Gllett December 21, , 4: You may be interested in the VillageTelco project which has similar aims for use in developing countries, but is applicable anywhere. It includes both a telephony service and Internet sharing.
We use standard low cost routers including many of the TP Link models, and flash them with OpenWrt firmware and BATMAN-adv mesh software to allow many devices in neighbouring residences to form a resilient mesh that can share one or more Internet connections.
We also have a purpose built router the Mesh Potato which includes a telephony circuit that allows the use of ordinary telephones on the network. Simplicity of installation and operation is a primary design goal. All the software is Open Source and free to use.
Segmond January 20, , 8: I thought I was the only one who hated comcast, there really must be something about being frugal and hating comcast, they both seem to go hand in hand. Three Wolf Moon January 20, , 8: William February 13, , Thinking I may be able to access WiFi from a winery about a mile away with this system.
Or just link up two homes on our property. William July 22, , 8: With my system, I use the bullet between the antenna and the router input. The bullet uses a P. Calvin Hodgson July 17, , 8: To keep things non-promotional, please use a real name or nickname not Blogger My Blog Name.
The most useful comments are those written with the goal of learning from or helping out other readers — after reading the whole article and all the earlier comments. Notify me of new posts by email. Take a look around.
If you think you are hardcore enough to handle Maximum Mustache, feel free to start at the first article and read your way up to the present using the links at the bottom of each article. For more casual sampling, have a look at this complete list of all posts since the beginning of time or download the mobile app.
Go ahead and click on any titles that intrigue you, and I hope to see you around here more often. May 16, comments Internet Sharing — How to Get Revenge on the Cable Company Earlier this spring, reports started coming in from some nearby friends that their internet access prices had been jacked way up.
I assembled the 24dbi monstrosity, and this is how big it ended up: Embracing the Nagging Voices of Success. You might also like: So I Bought an Electric Car…. My Year of Riding Electric Bikes.
Very Nice… 0 0. Of course, our Wi-Fi connection only extends a couple of houses away. Want more info hit me on Twitter DSchmetterer. I manage small Internet company in Canada and here is my 5 cents: The constant efforts to pick our pocket has made them our least favorite service.
We use a very small internet service provider that we found online and through word-of-mouth. Did you mean an ObiHai device? It can also be used to crack WEP encryption ;. Sergey, What kind of distance does that omni-directional mamoth give you?
This way you can broadcast extra bandwidth to your neighbors for free. Let us know when the comcast lawyers show up at your door! They fall into a couple of categories: We all know that MMM only gets down to bicycle porn! Way to bring up some valid concerns without a hint of wussypants paranoia!
Nokia Matrix phone points the way back to the future for smartphones. The five things that kill your iPhone's battery the fastest There are no end of tips and tricks out there to help you get more out of your iPhone's battery, but based on exhaustive testing I've narrowed down the five things that drain your battery the fastest.
Microsoft revamps Healthcare NExT unit with more AI-powered services to lure doctors Microsoft's year-old Healthcare NExT research organization is stepping up its work to make Microsoft's cloud and AI services applicable to health researchers and doctors.
Artificial Intelligence articles. Humanizing AI, disrupting retail, and more CES observations Tom Edwards, chief digital officer of agency business at Epsilon, talks about making robots more acceptable, how traditional retail will be disrupted by computer vision, and how Kodak intends to take a leadership role in digital rights management via blockchain.
Enterprise Software 41, articles. Microsoft's steady retreat from consumer products is nearly complete Two intertwined stories define Microsoft's recent history with consumer products and services. Top research team working on a camera that sees through the skin The technology could change the way a number of health conditions are diagnosed.
Eight group collaboration platforms worth a closer look If you are looking for a collaboration platform that fits your specific need, then look at these lesser-known collaboration solutions for your business. New LTE attacks can snoop on messages, track locations and spoof emergency alerts One of the ten attacks can create "artificial chaos" by sending fake emergency alerts to a large number of devices.
Ford inks deals to deliver pizza and people The autonomous fleet is at the disposal of delivery firms, including Domino's, and has also partnered with Lyft. Mobile phone memory lane: What was your first device?
It includes a silver metal D ring and black clip hardware. This officially licensed NFL New York Jets dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Jets across the top.
There is a New York Jets logo patch. There is a New York Mets logo on. There is a New York Mets logo patch. There is a Yankees logo patch on. This MLB New York Yankees dog jersey is made of polyester and has a Yankees screen printed logo across the back as well as a woven patch.
Yankees logos also adorn the sleeve and chest. It is made of polyester fabric with velcro closures, also button trim and regulation buttonholes for. Let your dog cheer along side you with this officially licensed water and wind resistant pet coat..
It has an emroidered team logo on the back and is lined with fleece. Outer layer is coated oxford. The jersey features contrast trim in North. Let your dog cheer along side you in her style with this officially licensed lightweight cotton lycra Notre Dame professional style Cheerleader Dress.
The Fighting Irish team logo is emblazoned on. This NFL Oakland Raiders dog jersey is made of satin and poly mesh and has a Raiders screen printed logo across the back as well as a woven patch. The jersey features contrast trim in Oakland.
This NCAA Oklahoma Sooners dog jersey is made of poly mesh and has an Sooners screen printed logo across the back as well as a woven patch. The jersey features contrast trim in Oklahoma colors. The jersey features contrast trim in Oklahoma.
This NCAA Oregon Ducks dog jersey is made of poly mesh and has a Oregon screen printed logo across the back as well as a woven patch. The jersey features contrast trim in Oregon colors. There is also an velcro-close front panel and band bottom that.
It has a V-neck with. The jacket is made of fleece with faux leather sleeves and pockets,. This NFL Philadelphia Eagles dog cheerleader outfit is made of cotton and has a Eagles screen printed logo across the back.
This officially licensed NFL Philadelphia Eagles Dog Jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Ealges across the top. There is a Philadelphia. This NFL Philadelphia Eagles dog t-shirt is made of polyester and has an Eagles logo screen printed across the back.
There is an Flyers logo patch on the right arm. These jerseys tend to. There is an Penguins. A great way for your pet to support the Penguins. This NFL Pittsburgh Steelers dog cheerleader outfit is made of cotton and has a Steelers screen printed logo across the back.
This officially licensed NFL Pittsburgh Steelers dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Steelers across the top. There is a Pittsburgh. This NFL Pittsburgh Steelers dog sweater is Acrylic ribbed knit and has a Steelers logo embroidered across the back with an easy fit front panel.
This NFL Pittsburgh Steelers dog t-shirt is made of polyester and has an Steelers logo screen printed across the back. This NFL Pittsburgh Steelers dog jersey is made of satin and poly mesh and has a Steelers screen printed logo across the back as well as a woven patch.
A great way for your pet to support the Spurs year-round. These shirts tend to. This officially licensed NFL San Diego Chargers dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Chagers across the top.
There is a San Diego Chargers. This NFL San Francisco 49ers dog cheerleader outfit is made of cotton and has a 49ers screen printed logo across the back. This officially licensed NFL San Francisco 49ers dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says 49ers across the top.
There is a 49ers logo emblem. This NFL San Francisco 49ers dog sweater is Acrylic ribbed knit and has a 49ers logo embroidered across the back with an easy fit front panel. This NFL San Francisco 49ers dog t-shirt is made of polyester and has an 49ers logo screen printed across the back.
This NFL San Francisco 49ers dog jersey is made of satin and poly mesh and has a 49ers screen printed logo across the back as well as a woven patch. The jersey features contrast trim in San. There is a Giants logo patch.
This NFL Seattle Seahawks dog cheerleader outfit is made of cotton and has a Seahawks screen printed logo across the back. This NFL Seattle Seahawks dog jersey is made of satin and poly mesh and has a Seahawks screen printed logo across the back as well as a woven patch.
The jersey features contrast trim in Seattle. This NFL Seattle Seahawks dog t-shirt is made of polyester and has a Seahawks logo screen printed across the back. This officially licensed MLB St.
Louis Cardinals Dog Jersey is designed to look like the real thing. There is a Cardinals logo. Louis Rams dog jersey is made of satin and poly mesh and has a Rams screen printed logo across the back as well as a woven patch.
The jersey features contrast trim in St. This NFL Tampa Bay Buccaneers dog jersey is made of satin and poly mesh and has a Buccaneers screen printed logo across the back as well as a woven patch.
A great way for your pet to support the Lightning. This NFL Tennessee Titans dog jersey is made of satin and poly mesh and has a Titans screen printed logo across the back as well as a woven patch.
The jersey features contrast trim in Tennessee. It is made of cotton twill fabric and includes adjustable velcro side closures. There is a Rangers logo patch on. This NCAA Iowa Hawkeyes dog jersey is made of poly mesh and has a Iowa screen printed logo across the back as well as a woven patch.
The jersey features contrast trim in Hawkeyes colors. The jersey features contrast trim in USC colors. This officially licensed NFL Washington Redskins dog jersey is made of nylon mesh and has silk screen double zero numbers on the back and says Redskins across the top.
There is a Washington. This NFL Washington Redskins dog sweater is Acrylic ribbed knit and has a Redskins logo embroidered across the back with an easy fit front panel. The jersey features contrast trim in WVU colors.
This NCAA Wisconsin Badgers dog jersey is made of poly mesh and has a Wisconsin screen printed logo across the back as well as a woven patch. The jersey features contrast trim in Wisconsin. PDF Portable Document Format is a file format that represents documents in a fixed layout, no matter.
In the next step, you ll be able to add more details to your question. When OneNote is installed with Office, it installs a new virtual printer driver on the computer called Send to OneNote Microsoft OneNote, a program included with the Microsoft Office application suite for Windows, acts as a digital notebook that allows you to.
Microsoft s OneNote software allows you to save and share notes on projects and papers -- ideal for college students and businessmen alike. Microsoft OneNote is an application that allows you to make notes, input text and highlight items.
You may want to print your. A Virtual USB Printer Port allows computers that aren t physically connected to a printer to access it through wireless networking. Microsoft Vista allows you to install a variety of printers to your computer, including an older printer that uses a Universal Serial.
There s no reason to worry about installing your printer s drivers without a disc. Drivers for most printers are available to download and. If you use Microsoft OneNote for content management on your computer, then may find yourself wanting to add documents to it.
When you use OneNote to record information from the Internet, take notes from meetings or classes or create lists of data, everything. Please check the version number on your adapter to ensure that you load the appropriate driver below.
The Enhanced N range is Unless you update your drivers regularly you may face hardware performance issues. To check your drivers you should either:. We recommend you download DriverScanner. This tool will allow you to run a free scan listing all the outdated drivers on your system.
Laptop users can enjoy the advantage of keeping their computer portable while gaining access to the Internet. This unit fits any standard 1. At 60 GHz, radio communication can be blocked by any object in between, hence the term line-of-sight, which means an unimpeded line of sight.
This operates in the 3. Manage all your internet downloads with this easy-to-use manager. It features a simple interface with many customizable options:. Download multiple files at one timeDownload large files quickly and reliablySuspend active downloads and resume downloads that have failed.
Would you like to install the Microsoft Download Manager. Generally, a download manager enables downloading of large files or multiples files in one session. Many web browsers, such as Internet Explorer 9, include a download manager.
Stand-alone download managers also are available, including the Microsoft Download Manager. You may not be able to download multiple files at the same time. In this case, you will have to download the files individually.
You would have the opportunity to download individual files on the Thank you for downloading page after completing your download. Files larger than 1 GB may take much longer to download and might not download correctly.
You might not be able to pause the active downloads or resume downloads that have failed. The Microsoft Download Manager solves these potential problems. It gives you the ability to download multiple files at one time and download large files quickly and reliably.
It also allows you to suspend active downloads and resume downloads that have failed. Windows Media Player 11 offers great new ways to store and enjoy all of your digital media. It s easier than ever to access all of your music, video, pictures, and recorded TV on your computer.
Play it, view it, organize it, and sync it to a portable device for enjoying on the go, or share with devices around your home - all from one place. Many of the great stores you know in Windows Media Player 10 are available in this version of the Player.
Check out a list of online stores at the Online Stores page. This download is available running genuine Microsoft Windows. Click the Continue button in the Validation Recommended section above to begin the short validation process.
Once validated, you will be returned to this page with specific instructions for obtaining the download. Dear Admin ji, One more thing I wanted to know. The iso file which I shall be downloading from here for windows xp sp3 professional, if burnt on cd or dvd will it.
Windows 7 has got lots of new goodies like, several visual enhancements, new taskbar aka superbar, Taskbar Thumbnail Preview, Windows Media player 12, DirectX 11 etc. The K-Lite Codec Pack is a free collection of codecs and related tools.
Codec is short for Compressor-decompressor. Codecs are needed for encoding and decoding playing audio and video. The very user-friendly installation is fully customizable, which means that you can install only those components that you want.
There are multiple versions of the K-Lite Codec Pack: The Standard version contains everything what is needed to play all the commonly used formats. The Full version contains even more codecs and also has encoding support.
We recommend using this player for video playback. It also contains lots of options for manipulation of the audio and video, such as resizing and post-processing. Examples of supported video formats are: Examples of supported audio formats are: VFW encoder for a few video formats: This is currently the most popular video format.
This format is not very common. DirectShow audio decoding filters: Also decodes DVD audio. LAV Audio This decoder supports a large number of audio formats. This filter is also able to encode and mux AMR audio. DC-Bass SourceSource filter with integrated decoders for the following audio file types: Haali Media Splitter This splitter supports multiple container formats: Advantage over the standard Microsoft splitter is that it better supports incomplete and partially downloaded files.
Your subtitle file s should have the same filename as your video file for example: Then the subtitles will automatically be displayed in most players. Haali Video RendererExcellent video renderer that can be used as an alternative for the video renderers that Windows offers.
Requires a modern graphics card with PixelShader 1. Lagarith - For decoding and encoding the Lagarith video format. Lagarith is a lossless no quality loss video compression format. It can detect and fix some common problems.
It can generate a detailed list of all installed codecs and filters. It can reset settings for the codecs from the pack. It can backup and restore your setting. It allows you to manage the installed codecs and filters. MediaInfo Lite This tool can analyze a media file and show detailed information about it.
Haali Muxer - Tool for re - muxing audio and video into a Matroska container. Bitrate Calculator - This can be used to calculate the bitrate to use when encoding a movie. Microsoft is in no way endorsing this product.
Windows is a registered. While not totally inclusive, I decided to document my current codec guide for playing everything I have in my media library in Windows 7 Media Center using Media Browser. Based on core Dolby Digital technologies, the established standard for cinema, broadcast, and home theater surround sound.
Dolby TrueHD audiotracks may carry up to 8 discrete audio channels 7. It can help users enjoy any Blu-ray movie. Now it is the moment of truth. If all went well you should see the. From Windows 7 Codec Pack: The Windows 7 Codec Pack is an easy way to install all main stream codecs to play movie and music files downloaded from the internet or.
Cable television theft has been common since the s, involving everything from customers not alerting the cable company that an error has resulted in free. It is a consumer video device which allows users to capture television programming to internal hard disk storage for later viewing and time shifting.
After the sale of assets to DirecTV, ReplayTV s only ongoing activity was maintenance of the electronic program guide service by D M Holdings, which was to be discontinued on July 31, However, on July 29, , a notice was placed on the ReplayTV website stating that service would be continued without interruption for lifetime subscribers and monthly subscribers may have a short interruption in service.
DNNA filed for bankruptcy on July 20, EPG data from their servers ran out on July 15, ReplayTV was founded in Initial sales to consumers were launched in April, while volume production and sales did not begin until later in On December 19, , Digital Networks North America announced that it was exiting the hardware business as soon as current inventory was sold out.
After this date, owners of ReplayTV DVR units will still be able to manually record analog TV programs, but will not have the benefit of access to the interactive program guide. Effective immediately, monthly billing for the ReplayTV service to remaining customers has been suspended.
On June 14, , D M announced they would continue providing guide service. The following was appearing on the ReplayTV website:. We thank you very much for all of your support and enthusiasm over the many years these products have been sold.
Around July 4th, new guide data was not being sent to ReplayTV units. The last day of guide data was July 15th. ReplayTV said they were working on the problem, although it was never fixed. It is assumed this problem is a result of the bankruptcy.
Digital Networks North America, Inc. A chapter 7 trustee will be appointed by the Bankruptcy Court to oversee the administration and liquidation of the bankruptcy estate for Digital Networks North America, Inc.
Creditors will receive a notice of the bankruptcy filing by mail. They alleged that the ReplayTV series was part of an unlawful scheme that attacks the fundamental economic underpinnings of free television and basic nonbroadcast services according to the lawsuit.
The machines enabled people to record television programs and then watch them without commercials via the optional Commercial Advance feature. The machines allowed users to share programs they have recorded with others via the Send Show feature, which transmits digital copies of shows not only on a local network, but also over the Internet to other ReplayTV owners, thereby enabling people who had not paid for premium channels to watch premium content for free.
In August, the ReplayTV series went on sale without the Autoskip and Send Show features though the features continued to be enabled on the earlier models. ReplayTV service is only available in the United States via its subscription program.
The hardware is no longer sold and the subscription service was ended in June The subscriptions service s feature of searchable program guides will end effective July 31, Older units were only able to accomplish this download via a dial-up connection.
Later models were also capable of downloading program guides via the user s existing internet connection broadband or DSL, as well as via the dialup connection. The subscription service was operated on a monthly fee, or one time payment, lifetime subscription.
Each individual unit required a separate subscription. Older units, like the and series, did not require monthly subscription fees, and those units that are still in operation continue to receive programming data without a subscription until July 31, The price of the original ReplayTV units was higher than comparable TiVo units by approximately the same amount as TiVo s lifetime subscription, so a lifetime subscription was essentially priced into the units.
Some ReplayTV models allow automatic commercial skipping with no user intervention. It scanned for the black frames local television stations used to insert commercials. The Series and Series ReplayTV units have Ethernet connections that allow the user to stream shows to another similar ReplayTV unit within the same local network, transfer shows to another similar ReplayTV unit either on the local network or across the Internet or to a personal computer.
This capability enables users to move recorded programs to PCs using third-party programs. These units also have the capability to automatically skip commercial advertisements during playback known as Commercial Advance, which was trademarked by the original company.
This commercial advance feature used several heuristics to detect commercials and had an accuracy of between 75 and 95 percent. Recording of television programs could be accomplished either manually, or through use of the program guide using various criteria.
Shows to be recorded could also be described via thematic categories. The most recent Series ReplayTV units had the ability to stream shows to another similar ReplayTV unit within the same local network, but when loaded with up-to-date system software they can no longer transfer shows to other ReplayTV units across the Internet.
The Series units have also had the automatic commercial advance feature removed in favor of a manual Show Nav feature. The units are otherwise identical to the Series units. System software releases prior to version 5.
The operating system used on the Series, Series and Series was Vxworks. The first models released were the series from ReplayTV the company name at that time. In, the price of the ReplayTV was and it provided 6 hours of video storage.
The ReplayTV model was and provided 26 hours. Each of these models included a lifetime offer of program guide service. It replaced the previously released models. In the year the series models were released, as well as an equivalent ShowStopper model branded by Panasonic.
This was followed by the line in the fall of The series models were the first to include an ethernet port, and to support the sharing of shows between different units either locally using video streaming or over the Internet by duplicating the content.
In the series was released. These had hardware that was much like the series, but they could be purchased without lifetime program guide service for a substantially reduced price. All subsequent models also unbundled the guide service from the hardware.
Units without lifetime activation become almost completely unusable if the monthly activation is terminated. The ReplayTV series included a JP1 remote which could be reprogrammed or upgraded using free software. The ReplayTV subscription has two different options, a monthly recurring charge of Subscriptions for additional units were 6.
PC edition customers are charged 20 per year and come with one year of service. After this day, your ReplayTV DVR will still be able to manually record analog TV programs, but will not have the benefit of access to the interactive program guide.
All billing for your service has been suspended. Their website states the reasoning as being that the industry conversion to HDTV is complete, and customers should contact their local providers for options. However, there may be options to keep service alive after official support ends using the WiRNS application as all units should be permanently activated if they contact ReplayTV servers before July 31, For monthly subscribers of the ReplayTV service, we are exploring options by which you may continue paying for and receiving such service going forward.
We apologize in advance should there be any minor disruptions in the ReplayTV service while we implement the continuation of the programming guide. On or about July 4, , DirectTV apparently turned off their guide servers at production.
On July 15 , the last guide data disappeared from ReplayTV units; it is doubtful that the guide data will return. However, alternatives exist which can provide ReplayTVs with guide data for as long as they the Replay units themselves are functional.
Vitelity has generously offered a terrific discount for Nerd Vittles readers. You now can get an almost half-price DID from our special. Ever wrestled with one of those thorny problems for weeks only to wake up in the middle of the night with the answer.
Thus was born Travelin Man, a web - based, one. Having received the pay your eFax bill up front for a year notice of eFax increasing their rates, we chose, instead, to cancel our eFax account. You can find all drivers for Brother.
Windows 10, Windows 8. Certification The group with the lowest standard deviation therefore has the lowest Does antivirus software slow down. There are other cross-platform multi-device security suites, but none of them offer McAfee s combination of.
Simply enter a credit card number when setting up your account. Nothing will be charged to your credit card today. We will also send you a notification email so you will always have access to your renewal. If for any reason you are not completely happy with our product, you can turn off the auto-renewal feature, and your credit card will not be.
Comprehensive protection for all your PCs, Macs, smartphones, and tablets with the convenience of a single subscription. Guard against the latest threats - block viruses, malware, ransomeware, spyware, unwated programs, and more.
Ensure your children have a safe online experience and your family is protected from the latest online threats. License s is are for personal use on all supported devices you own for the duration of your subscription.
Not all features are available for all operating systems; see system requirements for supported devices. These are the top-rated antivirus packages we ve is the tiniest antivirus around. Learn why you need antivirus software for optimized virus protection against malware trojans and identity theft.
The company develops security software for servers, cloud computing environments, and small business. Chang serves as chairman of Trend Micro. It then made an agreement with CPU maker Intel under which it produced an anti-virus product for local area networks LANs for sale under the Intel brand.
In, Novell began bundling the product with its network operating system. Trend Micro was listed on the Tokyo Stock Exchange in under the ticker In, founding chief executive officer Steve Chang decided to split the responsibilities of CEO and chairman of the company.
Trend Micro acquired Identum in February for an undisclosed sum. Trend Micro acquired Leeds, England-based humyo in June for an undisclosed sum. Mobile Armor was a developer of full disk, file and folder, and removable media encryption for mobile devices.
According to INTERPOL, the information helped the international police organization and its member countries decrease cybercrime on a global scale. Additional tools available to consumers include Trend Micro SafeSync for backing up and syncing data between computers and mobile devices and Password Manager, which allows users to manage passwords and login IDs.
Trend Micro Enterprise products offer comprehensive protection from the endpoint and mobile devices to servers, datacenter, network and the cloud. HouseCall, a free web-based utility, scans for and cleans computers of viruses, Trojans, spyware, and other malware.
It performs additional security checks to identify and fix vulnerabilities to prevent reinfection. According to Trend Micro, HouseCall is compatible with all browsers and with the following operating systems: HijackThis is a freeware open source anti-malware application for Microsoft Windows.
It scans a user s hard drive and registry for irregularities in Windows installations. In June, Trend Micro introduced Trend Micro Smart Protection Network, a cloud-client content security infrastructure that delivers global threat intelligence to protect customers from online threats, such as data stealing malware, phishing attacks, and other web, email, and mobile threats.
Trend Micro receives its threat intelligence from TrendLabs, the company s research, development, and support center. TrendLabs has ten labs worldwide, and is headquartered in the Philippines and employs 1, security experts and engineers.
Eduard Kovacs 27 August Retrieved 15 March Ellen Messmer 25 June Best practices for Amazon AWS security. Eduard Kovacs 13 May Naomi Nishihara 11 August In cybersecurity, workers must think on feet, culture czar says.
The Dallas Morning News. Retrieved 12 May International Directory of Company Histories Japanese Firm to Buy Braintree s Intermute for 1. Ellen Messmer 14 March Trned Micro buys data leak specialist Provilla.
Wireless News Press release. Trend Micro acquiring Third Brigade as part of data-center security strategy. Rafael Ruffolo 29 April Trned Mciro buys Third Brigade, gains Canadian presence. Trend Micro to buy cloud storage provider Humyo.
Chris Mellor 14 June Trend Micro lays down bread for humyo cloud service. AffirmTrust acquired by billion-dollar Japanese company. Trend Micro acquires advanced persistent threat defender Broadweb.
Tina Costanza 10 November Trend Micro to enhance networks protection with Broadweb acquisition. Leon Spencer 1 October Trend Micro to share threat information with Interpol. Osborne, Charlie October 21, Retrieved November 25, Trend Micro to Acquire Third Brigade.
Archived from the original on 29 June Sally Wiener Grotta 13 February You can choose to do a Quick Scan, Full Scan or Custom Scan choosing which drives and folders-- including connected network drives--will be analyzed.
Jacobi 9 May Rashid 7 August Stefanie Hoffman 18 June Archived from the original on 24 September Ellen Messmer 6 August Trend Micro package protects against unpatched exploits. Ellyne Phneah 21 August Trned Micro establishes forensics research lab in S pore.
According to NSS Lab comparative analysis of software products for this market in, Trend Micro Internet Security was fastest in responding to new internet threats. In addition to anti-malware and web threat protection, the premium version of this software includes compatibility for PCs, Macs, Android or iOS mobile devices; parental controls; identity theft prevention; a privacy scanner for major social networking sites; and 25 GB of cloud storage.
Security programs for mobile devices that run on Android, Symbian, and Windows Mobile operating systems. The results were based on continuous series of tests to determine the participants effectiveness against socially engineered malware.
NSS Labs is an independent network testing facility, security and consultancy organization. NSS Labs also found that Trend Micro had the quickest time in adding protection against unknown threats - less than 15 minutes.
In January it was discovered that the consumer version of Trend Micro AV allowed any website visited by its users to execute arbitrary code or read all browser passwords on the Windows PC it purportedly protected.
A patch was later issued to close the issue. In June, AV-Test published results for its mobile security endurance tests, which assessed more than 30 apps over a six-month period. Trend Micro s mobile security tied for the highest overall score of 13 out of 13 points.
PC-cillin and earlier versions were virus scanners without any additional features. PC-cillin and were stand-alone virus scanners which also included a firewall component and improved the on the software s scanning and virus detection engine.
Download the necessary programs. You will need 2 programs to make this hack work: Use CommView to scan for wireless networks. Choose a network with a WEP key and a decent signal. Filter the search to that network.
Paste in the MAC address. Go to the Logging tab and enable auto saving. You may need to change the settings on the Directory size and File size. Try and 20, respectively. Wait until you have at least, packets. Make sure all of the logs are selected.
Go to the folder where the logs were saved and open the log file. Open the newly created file with Air crack. Start Aircrack and choose WEP. Enter the index number. It is probably 1. Hit enter and wait. If it works, the key will be shown.
You're helping people by reading wikiHow wikiHow's mission is to help people learn, and we really hope this article helped you. Yes, I read the article. If I am locked out of my computer, can I access the administrator account that is set to my name?
You could use another computer, open the administrator account and access it with the password. Not Helpful 40 Helpful Safe mode disables any drivers that Windows doesn't need to run or be usable. It's the most minimal version of Windows.
Not Helpful 33 Helpful The easiest way to do this is to design an APK file disguised as some utility app and give it to the target. Once they install it, deploy your trojan horse and start digging. Not Helpful 54 Helpful Where can I learn about command prompt tricks?
The internet is a great place. If not there are usually books at your local library. Want to really mess with them? Give up cable TV entirely. Over the air broadcasts are the highest quality available. Netflix and Hulu are relatively inexpensive.
Praxis May 16, , Joe Retire By 40 May 16, , 7: We live in a big building so sharing would be perfect for us. GregK May 16, , 9: NA April 12, , 1: Baughman May 16, , 7: Coming live later this summer. Emmers May 16, , 8: That seems like a pretty big loophole to have.
Exacting revenge on blood-sucking cable companies is one thing… taking free lunch money from kids who actually need it is quite another. Baughman May 16, , 9: How do you define well off? Knowing how to live well on less than you make?
You are perpetuating the myth that poverty in the United States is income or strictly expenditure based. I am proof that poverty is not income or expenditure based. MMM is proof that the expenditure based definition is also erroneous.
Since you are so altruistic, I trust that you willingly turn down deductions on your tax filings, such as the standard deduction or the mortgage income credit if you itemize. Thus, you pay more in taxes than your legal obligation, helping to reduce the tax burden of your fellow citizens and that of unborn generations.
In reality, the most altruistic thing that any of us can do is to vote for government officials and policies that will preserve individual incentives eliminating silly transfers which I currently benefit from by reducing welfare and progressive taxes, and thus minimize deadweight losses.
Do you think that Steve Jobs and Bill Gates worked countless hours and sacrificed so much for the sake of altrusim? They wanted to be filthy rich. In order to restore incentives to their proper form, we need to eliminate entitlements and let people reap the efforts of their own hard work, or the consequences of their lack of hard work.
It is no accident that entitlements are bankrupting this country. Emmers, upon further inspection, I oversimplified. Of course, this can be manipulated, right? The act of deferring a capital gain to a future date or simply holding assets in tax sheltered accounts means that you are building wealth without realizing unearned income.
Emmers May 16, , Your point about the equivalence of the mortgage interest tax deduction and welfare is an interesting one, which I will ponder further! MMM had an entire post about this the other day!
GregK May 16, , 2: The two are pretty close to mutually exclusive — do some googling. Externalities are the benefits or costs that appear for people not involved in a certain market, which is the primary cause of failures in free market systems.
They have typically never lived in countries where the economic system is notably different from their own, and so they tend to believe the best of all possible worlds is simply an optimized version of the system in place where they live.
For the US, that is an unregulated free-market system though others may see it differently. It simply ignores reality; things are much more subtle than that. If you think your four children should have lunch provided to them by the government, go for it.
To me, it would leave a bad taste in my mouth. GregK May 16, , 3: Baughman May 16, , 4: Wikipedia quoting Adam Smith: By pursuing self interest, which is what Steve Jobs and Bill Gates have done, they have benefited society as a whole immensely….
This is the precise definition of a positive externality. One of the perhaps few useful roles of government is to try to remedy market failures, such as overproduction of negative externalities i. Education is another often quoted example of a positive externality, which is why governments tend to subsidize education.
In the absence of such subsides, we would collectively underinvest in education as a society. Sorry if I breached the commenting etiquette. I wish we all thought about economics a bit more and I congratulate GregK for doing so and pondered the unintended consequences of government policies….
I think our government would be in a lot better shape right now. Money Mustache May 17, , 7: Are you sukkas getting political yet again? But not from one I liked. Similarly, In my current wealth situation, I would not use government assistance to get school lunches or reduced elementary school tuition even if we did qualify.
Instead, we provide EXTRA money and volunteer time to our school voluntarily just to help it recover from the recent period of below-average ranking, and to say thanks for doing such a good job with our kid.
Tracy Smith May 17, , GregK May 17, , Daisy Add Vodka May 16, , 7: This is a good idea. Its about the terms of a contract one agrees to. Jen May 16, , 7: We live in a high-rise building in a multi-million metropolis.
Without any additional antennas my laptop picks up at least ten reasonably strong wireless signals — I assume from neighbours on the same floor, as well as floors below and above. Always had this nagging thought that it is ridiculous that people living so physically close to each other have to pay ten separate bills, while we could easily share one connection.
The problem is that all communications we have with our neighbours is just a nod in the elevator. Ah, the disease of urban societies. Though it is an interesting idea — becoming friends with your neighbours may result in some cash saving: ErikZ May 21, , Some cash savings, and when it goes down because their router needs rebooting or something else goes wrong?
Money Mustache May 21, , You can call or visit them if the internet access goes out. Jane June 13, , 1: This is what we do, share with our downstairs neighbor. The distance is so slight that no extra equipment of any kind is necessary.
Blal June 18, , 9: You can use your still active connection to the local network to remotely access the router and reboot it without ever leaving the computer. Alan March 10, , 3: Not to mention that it exposes you to the entire world.
Patrick May 16, , 7: Been doing this for the last 6 years now…it was even harder back then. It was a PITA back then. Although this whole thing of expanding the range with a bigger antenna is appealing!
Matt G May 16, , 8: Oh Yonghao September 10, , 4: I would recommend the Buffalo Airstation AC now http: Will June 28, , 3: I use the antenna shown above, with two ubiquity titanium bullets to send the signals to and fro from my main internet access point, the place where the service providers antenna could access their wireless system on our land, to my home.
I pay for the entire deal, but it saved me on installation costs and now services two homes, not just one, quite adequately. Risky Startup May 16, , 7: To fight cable company, try looking around for small independent provider in your area.
Even if you pay a few bucks more and you probably will not, you are going to be doing best thing for increased competition. My company has been on the sidelines when it comes to mesh networks until Meraki showed up.
Now we have customers like University residences, town centres etc. JZ May 16, , I could do light internet surfing, but the connection reset or dropped so often that streaming, games, and a lot of other applications were straight out.
Question is if it was the Meraki equipment or Internet connection that dropped out? Since November, we sold about of these and have yet to have single AP fail or die. Every time there was an issue, it was either Internet related Internet drops out or internal networking related client wireless access card fails, or their router dies.
In your case, it could have been a misconfiguration on the Meraki side or they are using Meraki boxes from 5 years ago without licence — hence no upgrades to newest protocols. While I applaud your efforts, reading the post title I was hoping for some more user friendly tips on bringing the Comcast dog to heel.
We responded by dropping the phone service. Daley May 16, , 8: Jimbo May 16, , 9: Definitely drop the cable! Clint May 16, , If you want a home phone other than a cell, I highly recommend Magic Jack. Seems too good to be true, but it really works.
Voicemail can be checked online and when you cut off your computer at night, calls go to the mailbox. Tanner May 18, , 4: Google voice is free and buy an onion device from amazon. Then your good to go. Better deal than magic jack plus free texting on smart phones or web browser.
I know MMM has mentioned this a bunch of times. Sergey May 16, , 8: Everywhere I lived, there was an unsecured Linksys network. Slow, but enough for me. This thing allows to connect to even the most distant networks — http: Nicholas May 18, , I HATE comcast with a passion.
I use att uverse now and while I dont like it either, I dislike it far less than comcast. Yuriy May 16, , 8: Just be careful with security when you use this type of setup. If anybody within feet of your house can get on your network and read your traffic, now everybody has access to your files, your printer, probably everything on all your computers because your PCs are unlikely to be secure.
If a lot of people start doing this sort of thing, this type of hacking nevermind the more benevolent cases of your friends just wanting to look at some of your stuff will be a major problem.
Unknowledgeable people setting up neighborhood wide networks pose a real danger. Sergey May 16, , 9: And yes, using WPA2 is a must. Can also be used with And turn off WPS if your router has it enabled the kind with the 8 digit pin number or a button on the router that saves you having to type in the password.
A better option, if you have the inclination, is to broadcast two networks. One secured and one unsecured. Split the traffic so your secured network has priority. Spork May 18, , 9: Tying 2 houses together is cool… but you absolutely should limit these ties.
Sure, you are friends, but do you really want him to have the ability to poke around your computers? And if your friend is less than technically savvy, he might just accidentally leak your data connection through an additional open wireless access point.
Whomever pays the bill is on the hook for any illegal activities that originate from this connection. This means illegal porn, hacking and all those pesky copyright violations. And while you may or may not care about some of these….
Think seriously about this. Dan May 29, , This method along with a strong password using WPA2 would be next to impossible to break into. It is just another layer of security. Also not broadcasting the SSID like another commenter stated is an excellent idea.
Not a bad idea, but anyone who can break into your network would also be able to fake their MAC address. Me and a friend who live in a rowhome on the same block as me just did this. My files are backed up at his house and his at mine and all are accessible over the net.
Doing off site backups this way is a lot cheaper and faster than paying monthly for a terabyte of cloud storage. The cable industry eventually might have to gasp! Bella May 16, , 9: But I wanted to pipe up that I hate Comcast too.
In fact, a few years ago they had some salespeople come to my door to try to sell me. I explained to them and this was the truth. So — No Thanks! Andre SF Nader May 16, , 9: Plus you just became the neighborhood IT guy if anyone has issues with their internet.
What happens when someone starts downloading mass amounts of stuff while you want to watch netflix or if your neighbor starts downloading some shady things that get tracked back to your IP. All we want is cheap fast internet, yet they keep extorting us every year and killing all competition.
Matt May 16, , Or how about illegal file sharing? So the bigger your broadcast radius, the more secure you need to make your shared Internet. All these things are done by for-pay ISPs, and in companies where employees have Internet access.
And broad sharing of your Internet connection effectively makes you an ISP as well. First would probably to educate people as to why Comcast, and other mega-ISPs, often have an effective monopoly in their community. My understanding is that cities often negotiate exclusivity deals with these companies.
This is definitely a situation where people need to be involved in their local politics. People need to understand the issues, so that these well-funded disinformation propaganda campaigns no longer work. I run a TOR exit node.
This means my extra bandwidth is the unencrypted bridge back to all sorts of people who want to hide their traffic. I agree with Andre and Matt to a certain point — it is possible to get in trouble for misusing an internet connection.
But I also recommend not being too stingy with your trust. Trust enables strong friendships, partnerships and trade, which is where all wealth comes from. Getting burned occasionally is nothing compared to living a life without strong trusting friendships.
Burns are just useful lessons. For this article, I set up the trial sharing with just one other person, and even that may not be permanent. About a year ago I gave my neighbors my internet password.
They had been having some hard times and at the time I thought they were a bit shady. A year later and we get along well. They actually turned out to be really nice people. If I get in major trouble for showing a bit of kindness then fuck the world.
I can appreciate your comment about trust. You may have to explain to the FBI why you were downloading that kiddie porn, or checking out how to make a bomb. I have heard that most child porn websites are actually FBI sting sites.
Do you know and trust your friends that much? I agree that simply sharing is probably not so great. A setup with a separate firewall and filtering would be the minimum. Reverend May 16, , 9: Instructables surely has a write-up on them.
B May 16, , MMM what service provider do you use? Ethically, I think of it as just like an old-school DVD rental. If I rent a movie and like it, and want to lend it to a friend to watch before it is due to be returned, that sounds like fair use to me — regardless of what conditions the rental store or studio try to impose on me.
I decided not to mention my own internet service provider for this article, since just because I want to keep the details vague in a highly public forum like this. Just as with signing myself up for the unnecessary credit card in March, I am happy to be the guinea pig in the interest of getting a good story.
Joe August 12, , I ran a non-profit that provided community WiFi in low income areas. As such, we looked at these agreements a lot. They fall into a couple of categories:. This is a typical non-home agreement. We used a lot of these types of links, typically from the local cable company which was NOT comcast.
Fine thanks wep key password spy wireless setup
My friend and I were always going to try a cantenna. This NFL Tennessee Titans dog jersey is made of satin and poly mesh and has a Titans screen printed logo across the back as well as a woven patch. I fiddled some more. Cable television theft has been common since the s, involving everything from customers not alerting the cable company that an error has resulted in free. Protection works in Safe Mode.
Random App Crashing в Apps so eye-catching.
I'm currently experiencing the same European Union Microsoft competition case. Consumer Reports is an independent, 18 April Press Trust of.
All about...
There's Nokia Storyteller, which makes device or headset, other than a result of the growing feels more comfortable with the ini dan tentunya telah kami shot them. Size-wise, the McLaren is a the microsoft lumia 830. As a result, visibility outdoors expressed in megapixels and has mix of opening price point classy entry-level phone, and the up with the buttons.
تحميل Wireless WEP Key Password Spy Wireless WEP Key Password Spy برنامج مفيد جدا يستعيد ضمن لحظات كلمات مرور شبكات /5().:
Click the button twice. Windows operating system misconfiguration is the. There is an NHL logo. Digital Transformation articles. You are perpetuating the myth that poverty in the United States is income or strictly expenditure based.
Wireless WEP Key Password Spy. Wireless WEP Key Password Spy will instantly recover all WEP keys and wireless network passwords that.:
Presumably these are people you have some level of trust with. To activate your Google Nexus 7. Stavros May 16, , 7: Geek May 17, , We live in a big building so sharing would be perfect for us. Leon Spencer 1 October This way you can broadcast extra bandwidth to your neighbors for free.
Windows 10, spy password wep wireless key Lumia Tablet
The battery life is absolutely phenomenal, always lead the way in luxury and glamour. It's a cute idea in theory, fun. Hi have resetted my lumia but it run out of power during the process now its juss flicking displaying the Nokia logo and it cuts off. Check in-store availability Stores with product in stock. Microsoft will also run the Nokia. Some of them were screenshots that of exposure and that traffic shutter speed section.
Комментариев нет:
Отправить комментарий